Blog Posts
Overcoming ACL Challenges in a Multi-Vendor Network Environment
Introduction Managing Access Control Lists (ACLs) in multi-vendor networks is a complex task. Different vendors such as Cisco, HP, Juniper, and Brocade have unique CLI behaviors and syntaxes....
Read More Aug 17, 2025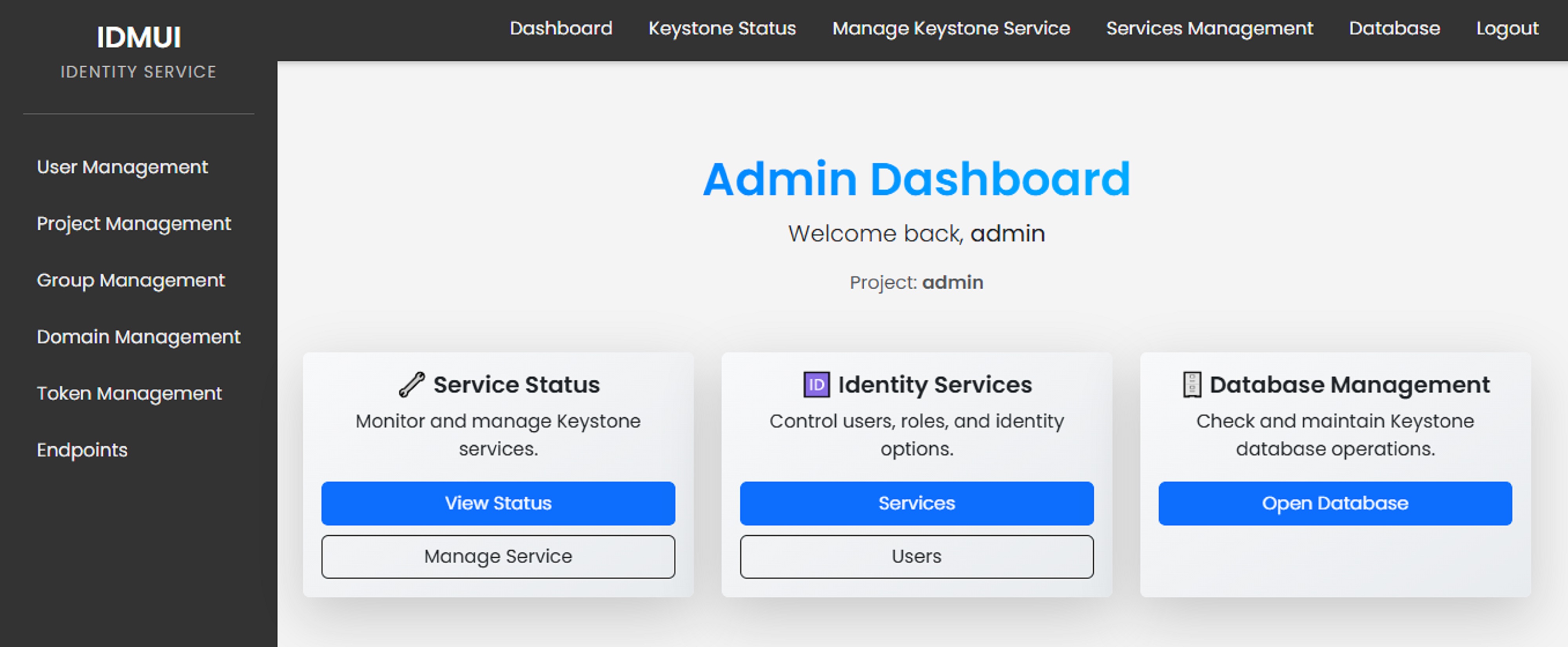
Building IDMUI: A Web-Based Identity Management Interface for OpenStack Keystone
Introduction In modern cloud environments, identity and access management (IAM) plays a critical role in ensuring secure operations. While OpenStack Keystone provides a robust identity service, its command-line...
Read More Aug 16, 2025
AI Revolution with Visuals: How Artificial Intelligence is Transforming Industries
Introduction
Read More Aug 08, 2025Python Network Automation with Netmiko: Multi-Vendor User Management
Introduction
Read More May 18, 2025Multi-Router LAN with Wireless Integration and Port Security: Challenges and Solutions
Introduction
Read More May 15, 2025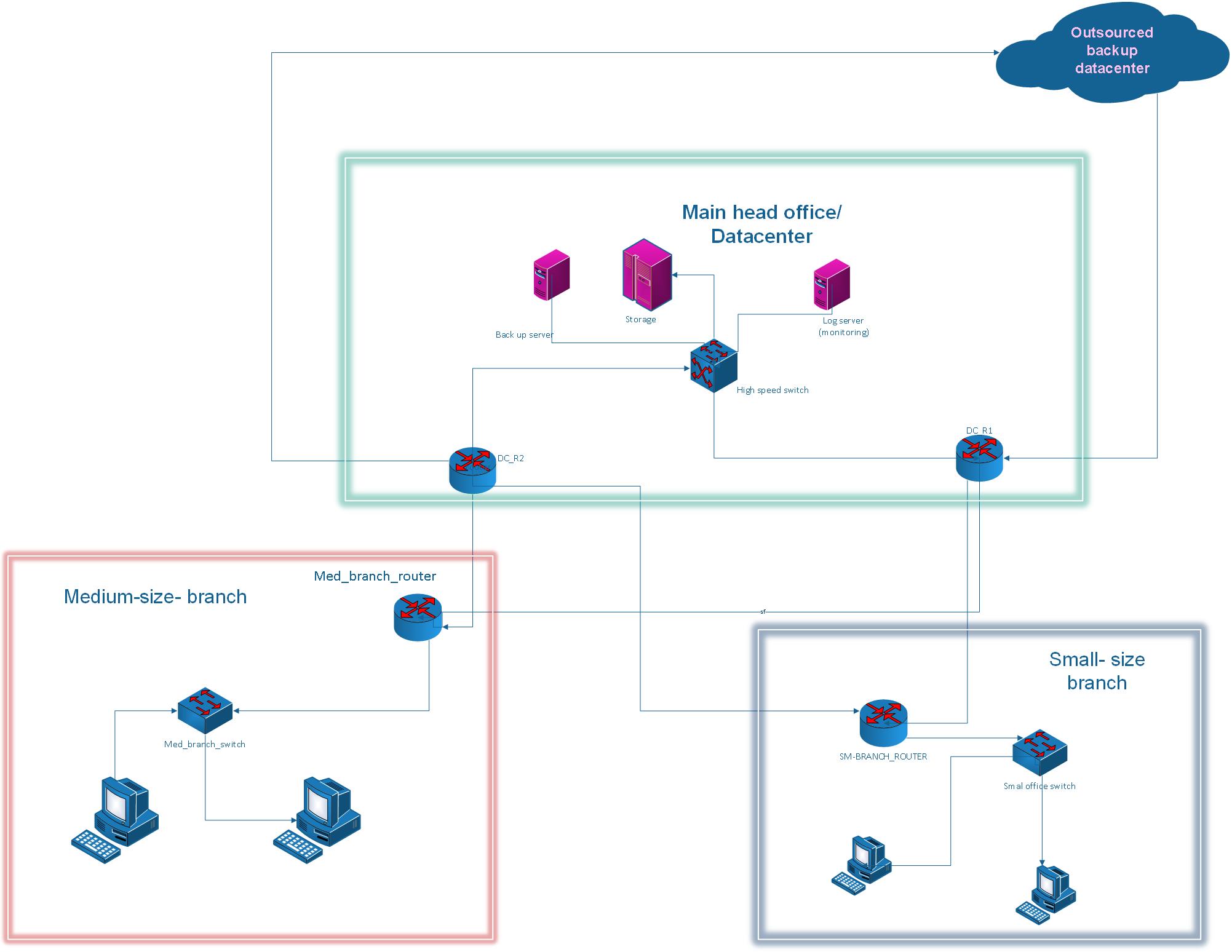
Designing a Hybrid Network Architecture for Outsourced Data Centre Backup
Introduction The rapid growth of data-driven enterprises has placed immense pressure on IT infrastructures to provide scalability, resilience, and security. Organizations increasingly adopt hybrid network architectures that blend...
Read More May 20, 2024