Introduction
In modern cloud environments, identity and access management (IAM) plays a critical role in ensuring secure operations.
While OpenStack Keystone provides a robust identity service, its command-line and API-based interactions can present a barrier for administrators and students who prefer a graphical, web-based interface.
The Identity Management User Interface (IDMUI) project addresses this challenge by delivering a Flask-powered web platform to manage Keystone services, projects, users, and roles with a focus on security, usability, and extensibility.
Research Motivation
The project was driven by three key gaps in existing OpenStack deployments:
-
Administrative Usability
Keystone is powerful but primarily CLI/API-based. A web UI simplifies operations for administrators, students, and researchers. -
Security and Compliance
Identity services are often the target of attacks. IDMUI implements Keystone-authenticated sessions, role-based access control, and real-time service monitoring. -
Integration and Extensibility
By using Python Flask and REST APIs, the system is modular, allowing future expansion into database management, real-time notifications, and PDF-based reporting.
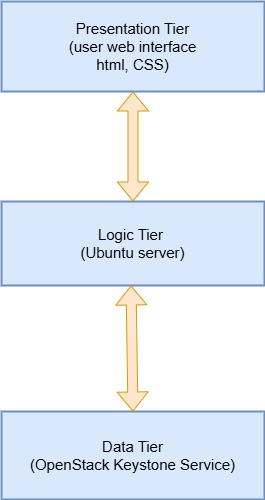
System Design
The IDMUI architecture is composed of several key layers:
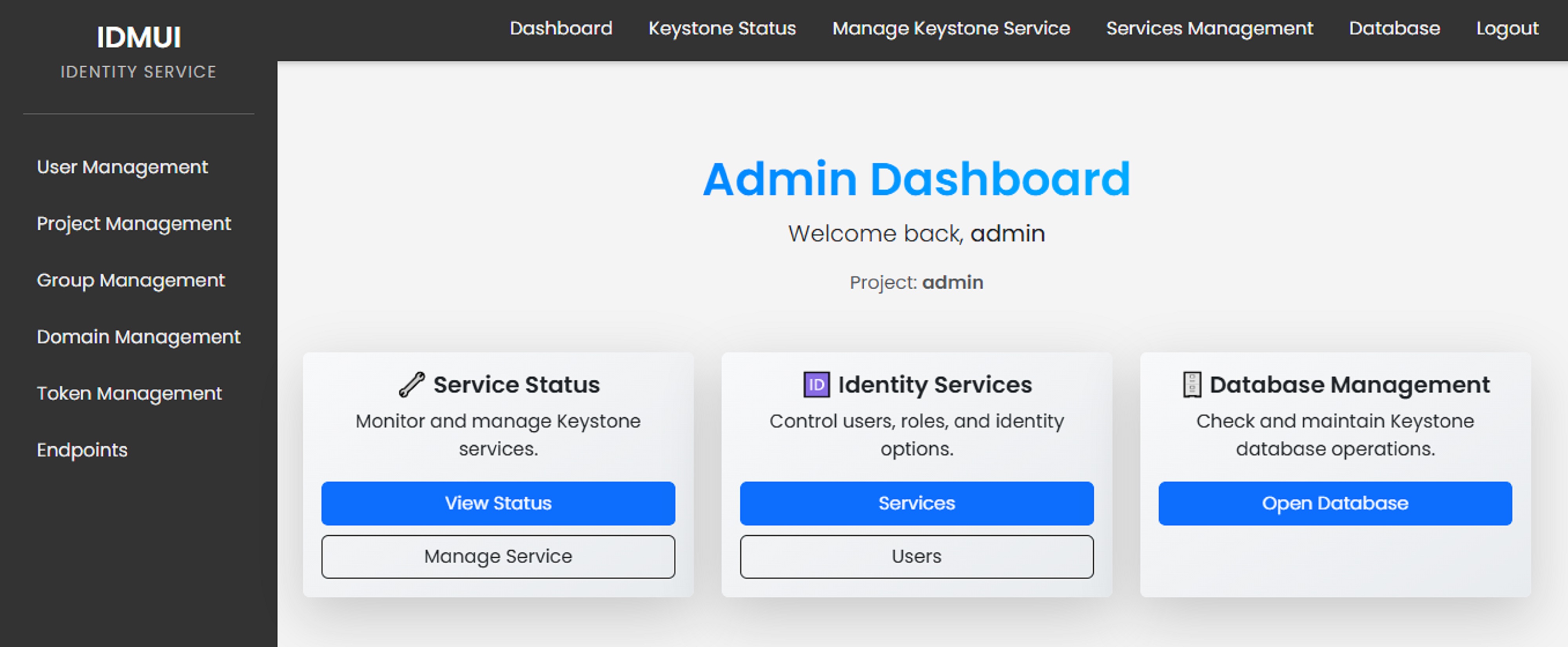
- Frontend (User Interface)
- Built with HTML, CSS, and Bootstrap for responsive design.
- Sidebar-driven navigation for Identity Service and Database Management modules.
- Flash messaging system for real-time feedback.
- Backend (Application Layer)
- Implemented in Flask (Python).
- Handles authentication, service communication, and session management.
- Uses modular routes for Keystone operations such as:
- User & Role Management
- Project Creation and Deletion
- Service Status Viewing
- Integration with Keystone
- Communicates with Keystone API for authentication and identity operations.
- Supports admin token authentication and role-based session tokens.
- Security Features
- Authentication enforced via Keystone.
- ACL-like restrictions for sensitive operations.
- Real-time service monitoring to detect downtime.
- Database Support
- Integrated with MySQL for storing application-level data.
- Future support for PostgreSQL or MongoDB as extensions.
Implementation Highlights
- Keystone Authentication
- Validates users by checking against Keystone’s identity store.
- Differentiates between admin users and regular users for UI access.
- Service Management
- Start/stop Keystone services remotely using Paramiko (SSH integration).
- View configuration sections such as
database,fernet_tokens,identity, andoslo_policy.
- User and Role Management
- Create, view, and delete users.
- Assign roles to users within specific projects.
- Real-Time Messaging
- Flash messages notify users of operation results (success/failure).
- Reporting
- Export user/project/service configurations into PDF reports.
Challenges and Solutions
-
Challenge 1: Secure Remote Operations
Solution: Used Paramiko SSH with strong credentials for server-side commands. -
Challenge 2: Session Management
Solution: Implemented session-based token storage validated against Keystone. -
Challenge 3: Responsive Design
Solution: Leveraged Bootstrap components for a professional, mobile-friendly UI.
Results
The IDMUI project achieved:
- Simplified Keystone Administration through a clean, intuitive web interface.
- Secure Access Control with Keystone authentication and role-based access.
- Operational Efficiency by integrating monitoring, user management, and configuration views.
- Educational Value as a learning tool for students working with OpenStack.
Lessons Learned
- A modular architecture (separating routes, utils, and configs) makes scaling easier.
- Security-first design is essential for IAM projects; integrating Keystone tokens early avoided major pitfalls.
- Frontend usability is as important as backend logic—users value intuitive design.
Conclusion
The IDMUI project demonstrates how research-driven design and implementation can extend the functionality of OpenStack Keystone into a secure, user-friendly, and educational tool.
By bridging the gap between CLI-driven operations and graphical interfaces, IDMUI provides real value for administrators, researchers, and students.
Source Code & Documentation: GitHub Repository (Coming Soon)
System Architecture Diagram: