Introduction
Managing Access Control Lists (ACLs) in multi-vendor networks is a complex task. Different vendors such as Cisco, HP, Juniper, and Brocade have unique CLI behaviors and syntaxes. In large environments, manual updates are error-prone and time-consuming.
This article shares my experience in updating ACLs across such an environment, highlighting challenges faced, solutions implemented, and lessons learned.
Environment Overview
The network included:
- Cisco Core and Access Switches
- HP Distribution Switches
- Juniper EX-series Switches
- Brocade Legacy Switches
Our goal was to apply consistent ACL updates across all devices without impacting production traffic.
Key Challenges
1. Multi-Vendor CLI Differences
Each vendor requires different command syntax and structure.
- Cisco uses standard/extended ACLs.
- HP separates ACL creation and interface binding.
- Juniper uses
firewall filterwith term definitions. - Brocade has both IP and MAC-based ACLs.
This required a careful, vendor-aware approach to ensure correct ACL application.
2. Juniper CLI Slowness
Juniper switches displayed slower CLI response times and required a different workflow to ensure commands executed correctly. Without proper handling, commands could be missed or fail silently, risking network outages.
3. Maintaining Network Stability
Updating ACLs on core or access devices has high stakes. Incorrect configurations could block production traffic or critical services. A robust testing and validation process was essential.
Solution Approach
Automation Strategy
To address these challenges, I implemented an automation workflow:
- Devices were categorized by vendor type.
- Vendor-specific ACL commands were applied to each device type.
- Juniper switches were handled with delays and prompt verification to accommodate slower CLI behavior.
- Logging was implemented to track changes and ensure auditability.
This approach allowed consistent, error-free ACL updates across a complex multi-vendor environment.
Testing and Validation
Before deploying changes to production:
- Scripts were tested in a lab environment.
- ACL behavior was validated using ping, traceroute, and interface monitoring.
- Rollback mechanisms ensured minimal disruption if issues arose.
Outcomes
- ACL updates were applied successfully across all devices.
- Manual errors were eliminated, and processes became repeatable.
- Juniper CLI slowness was effectively mitigated.
- The environment became more manageable and scalable for future ACL changes.
Lessons Learned
- Test before production – Multi-vendor environments are unpredictable.
- Understand vendor-specific nuances – Each CLI behaves differently.
- Plan for slower devices – Delays and prompt checks are crucial for reliability.
- Automation saves time and improves consistency – Critical for large networks.
Conclusion
Updating ACLs in a multi-vendor network can be challenging, but strategic planning, vendor-aware automation, and careful validation make it achievable. Addressing unique behaviors, such as Juniper CLI slowness, ensures reliable and consistent network security while minimizing risk.
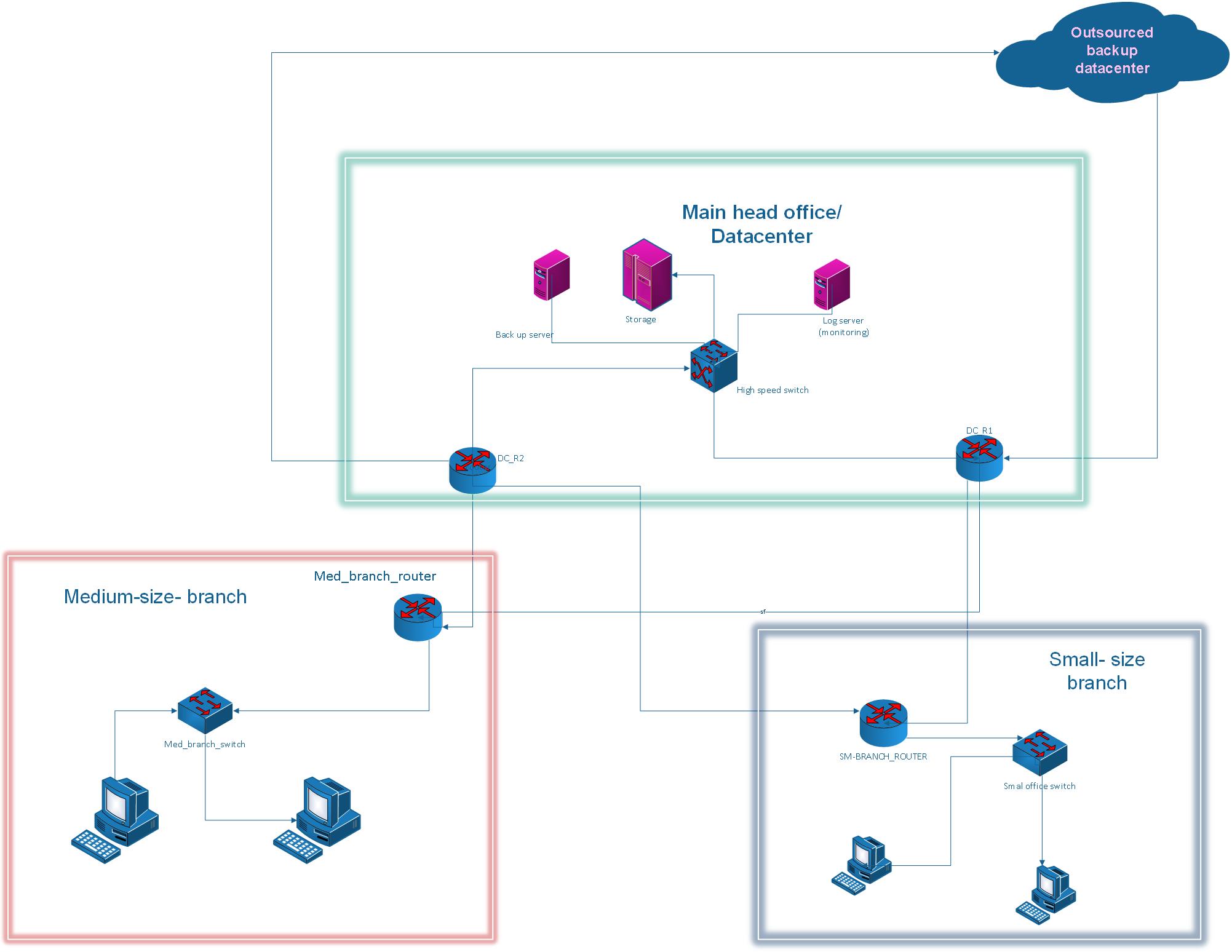
Network Diagram (Multi-Vendor Environment):